Managed Cyber Security Services You Can Trust
Join our Learning Center for the Latest Information

OPSEC COMPLETE - Cyber Security
All-in-One Security Bundles. Available including 6th Generation Security Stack Capabilities.

OPSEC COMPLETE
OPSEC Complete is a layered framework designed and applied to ensure your organization’s data is protected from digital threats and vulnerabilities.
To accomplish this, Cyber Security requires many layers of protective structure customized to meet your organizational needs. Each layer protects against the various points where threats are targeted: Application Security, Endpoint Security, Network Security, Cloud Security, and Information Security.
KDA Technologies uses the most effective methods to minimize enterprise-wide digital attacks from cyber threats. Whether you keep all your data in-house or on the cloud, each connection requires strict encryption and authentication. Organizations with comprehensive strategies enable them to monitor network traffic, identify incoming threats, and block, filter, or eliminate the attack.

Servers/Laptops/Desktops
Sales and Repairs
Business and Residential We have complete maintenance Programs Available

Technology is amazing
until it breaks!
Do you remember when you first got your new computer? How fast it responded to your every need. But as time passed, it slowed down, hesitated, or refused to move forward. Your time is essential, and trying to correct computer issues is something you cannot afford. KDA Tech Solutions can repair servers, laptops, and desktops of all makes and models.
From accessible part replacements to complex diagnostic solutions, we have experienced techs who will provide fast and effective computer repair services. We even offer proactive monitoring services for a small recurring charge.
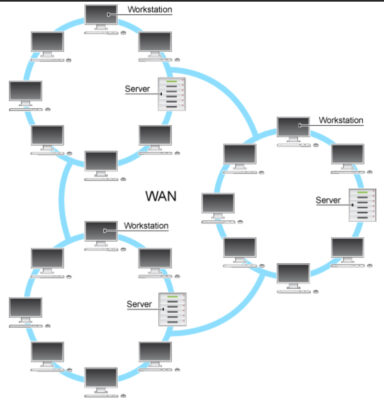
Network Design and Implementation
Decades of Trusted Experience, Designing, Connecting and Securing Networks.

Network Projects are made easier with KDA
It can be daunting if you want to install a new network, expand your business networking, or improve your existing design. It is difficult to know who will work with you step by step, from planning to execution. KDA Tech Solutions is here for you. We will work with you through every project stage to ensure you get the best network to fit your needs and increase your productivity. Projects of all sizes are given the attention needed to guarantee smooth operations, less downtime, simplified management, and improved security. With our in-house engineers and many decades of experience, we promise to deliver you the best and most secure connectivity you can get!

Cloud Services
Enjoy World Class 100% Encrypted Managed Backups.

Should We use Cloud Services
Cloud Services are methods for storing and sharing documentation and data over the internet with multiple users on multiple devices. It offers affordable access to various applications and resources without the company setting up special infrastructure or obtaining specific hardware.Most likely, you use cloud services without realizing it; third-party corporations that we use for email (Google, Microsoft, Proton, and Yahoo Mail are all examples) allow us to look read our email on our phones, computers, and or tablets no matter where we are as long as we have internet connectivity
There are three types of cloud service organizations: Public, private, and hybrid (a mix of both). KDA Tech Solutions will help you decide the best way to use this safely, privately, and securely; you will know that your data is protected by the most up-to-date and secure cloud partners.

Data Recovery Services
Software & White Room Recovery Services Available.

Have you ever worked on a project, hit a key, and the worst thing that could happen did: it disappeared? Or have you attempted to access a file on the server or on your own computer, and it no longer exists? We may be able to help.
At KDA Tech Solutions, we are experienced in recovering deleted files, accidentally reformatted drives, and corrupted file systems.We have many years of experience in recovering lost data for our clients. With access to a white room, we can get you a free quote and assessment of exactly what would be recoverable before you decide what you would like us to do. The only thing you pay is return shipping on your hard drive if you choose not to recover the data and would like your drive returned to you.
As we all know, an ounce of prevention is worth a pound of cure! KDA Tech Solutions also offers top-of-the-line disaster recovery planning and backup options. Please contact us to learn how we can help you today, before it is too late!

VoIP Phone Systems
100% United States Based Hosting and Support Platforms

VoIP, which stands for Voice over the Internet Protocol, is very much like having a landline service that uses the Internet to carry the signal. They can be used at any location that has an internet connection. They are often utilized in areas that have spotty service for cell phones.
VoIP Phone Systems are more robust and feature-rich than standard phone systems, replacing the bulky old PBX systems that most older businesses use. Our system offers the options of a mobile app, web browser calling, or your typical handset desk phone. The system also offers video conferencing and SMS capabilities, auto attendant(s), and much more. We can get you a new number, or you can bring one with you!
USA based Website Design and Hosting Platforms
What should a business leader consider when deciding on a website design company? What should they do to get Google to see and share the website? How do you reach your target audience securely?
See your ideas come to life on a website customized to meet your needs.

What we offer
We are a US-based web hosting corporation. All our workers are US-based and vetted. The security of your website is our highest priority, and we have taken measures to ensure that your website will continue to run during the worst of times. Redundancy with servers is only one method to ensure the integrity of your site.
Combining our secure data center sites (located in Pennsylvania) with our longstanding technical expertise has made the best alternative for business entrepreneurs who do not like the idea of their data existing outside the country. We do not want to be the largest – we want to offer the best service for our USA-based clients.

Full Service Sound Systems
Whether your project is a large church, sound stage, or private residence, KDA will give their full attention to the details - ensuring the highest quality available.

Your Audio/Sound Solutions
We can design, install, and configure AV solutions for any project, including:
- Multimedia Rooms
- Sound System Installations
- Online Conferencing & Document Sharing
- Projection Systems
KDA knows that every installation is different. We offer single or integrated services to meet your specific needs.
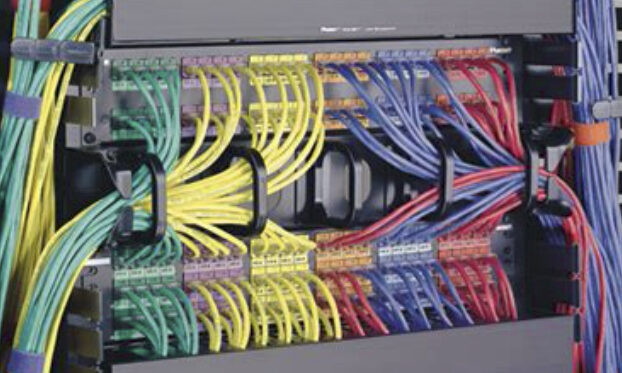
Full Service Construct Cabling
Whether you’re residential, a small business, a large corporation, a data center, or a government agency, we will provide reliable, high-performance data connectivity solutions delivered on time, within budget, and at the performance specifications required by today’s technologies.

Attention to Detail and Thorough Planning
Our comprehensive wireless surveys provide the insight that enables us to implement an optimized wireless network. Our surveys consider
- Power Requirements
- Wiring Needs
- Radio Frequency Coverage/Holes
- Access Point Placement
- Radio Frequency Interference

Business Leaders Guide to the Internet of Things (IoT)
The Internet of Things (IoT) is a network of interconnected “smart” devices (like sensors, cameras, and machines) that are connected to the internet. These devices collect and exchange data and make decisions without the need for human intervention.
Growing IoT technology adoption has opened the door for high-level security risks and threats, especially those that are tough to defend against because of flaws in many IoT devices.

The Two Sides of Al In Cyber Security
Managing a business on your own is challenging enough without worrying about cyberattacks. However, there is cause for alarm as hackers are using artificial intelligence (AI) to launch sophisticated cyberattacks to steal your data and disrupt business operations.
The good news is that you can take steps to protect your business. This info text will explain how Al is used in cybercrime and how you can safeguard your business.

Security Awareness - Your Small Business’ Best Investment
Employees are at the heart of your company’s security. They are the last line of defense against cyberattacks. However, they can also be a vulnerability. When an employee makes a mistake, like mishandling data, clicking on a malicious link, or giving a cybercriminal their password, they are opening the doors to expensive compliance failures and security nightmares for your organization.


